Combolists are getting better
Combolists – large lists of stolen login credentials – are integral to the contemporary cybercriminal ecosystem. In the past, these lists primarily consisted of pairs of usernames and passwords from older breach data that were compiled together and dumped onto platforms like Pastebin and traded as text files on the dark web. Criminals would then use them to bruteforce account logins and hope to get lucky.
Today, however, combolists are increasingly populated by fresh, actively-used credentials harvested directly by infostealer malware, significantly amplifying the risk posed to individuals and organizations alike. There is much more focus now on the creation and distribution of URL:Login:Password (ULP) combolists, compiled lists of credentials consisting of URLs, email or username logins, and passwords that are usually derived from stealer logs.
Attackers use these more timely and accurate ULP combolists in credential stuffing attacks targeting personal emails, social media, banking accounts, and corporate domains.
The evolution of the combolist
Since our previous analysis published a few years back, the combolist ecosystem has continued to evolve, becoming faster, more sophisticated, and considerably more dangerous. The pivot to ULP combolists is likely a result of a few different trends in the behavior of users, defenders, and cybercriminals:
- Users are more aware of password reuse and more likely to use password managers which generate new unique passwords for every account
- IAM policies are more likely to require “strong passwords” or prevent password reuse of previously compromised passwords
- Security teams are more likely to store passwords in difficult-to-crack hashing formats with salting, making it more rare for data leaks to contain large sets of plaintext or easy-to-crack passwords
- Infostealers, which steal usernames/emails, passwords in plain text, and URLs (in addition to lots of other data) are growing in popularity
In this post, we’ll outline the transformation of combolists, provide an overview of the stealer malware ecosystem, describe the lifecycle of compromised credentials, and recommend actionable steps that security teams, executives, and everyday netizens can adopt to mitigate this rising threat.
Understanding infostealers: The modern fuel of combolists
The rapid proliferation of combolists is predominantly driven by infostealer malware like LummaC2, RedLine, and Atomic Stealer. Infostealer malware silently infects victim machines, meticulously extracting sensitive user data – everything from browser-stored passwords and session cookies to autofill information, cryptowallet keys, credit card details, and even saved credentials for remote applications.
What makes this form of data extraction especially troubling compared to traditional breaches is the immediacy and novelty of the compromised information. Older breaches typically involve credentials that are already outdated or reset by the time they’re circulated on the darknet, limiting their practical utility for threat actors. Contrary to this, malware logs populated with user data from infostealers provide attackers with recently harvested, valid plaintext credentials often accompanied by precise timestamps to clearly indicate their recency, and by extension, their value.
The timeliness of these credentials amplifies their market value exponentially, dramatically increasing the risk of immediate or severe harm to both individuals and organizations. High-profile incidents, such as ransomware attacks, illustrate just how quickly this threat can escalate – infostealers like LummaC2 alone have successfully exfiltrated billions of credentials, often flooding underground markets within mere hours from the time of initial compromise.
It doesn’t take long for that exfiltrated data to end up in the hands of initial access brokers, who can then sell that access to ransomware operators. SpyCloud found that nearly one-third of companies that experienced a ransomware event had at least one infostealer infection in the preceding sixteen weeks leading up to the attack.
The following screenshots illustrate the typical contents of stealer logs; this example was discovered in early 2025 and was derived from the LummaC2 infostealer.
Exfiltrated victim data is typically organized by IP address. Every folder in the screenshot above represents one unique victim wherein the exfiltrated data for each machine is stored. These logs usually contain hundreds, if not thousands, of unique victims.

In nearly every stealer log, data exfiltrated includes running processes, installed software, and a litany of system specifications and user information.

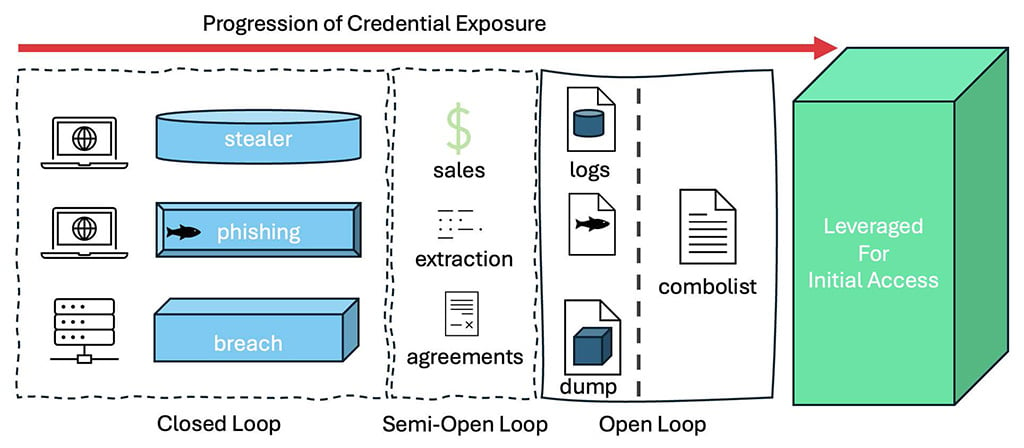
The stealer-to-combolist pipeline
The pipeline from stealer infection to usable credential data is streamlined and highly automated. It begins when a victim unknowingly executes malware – often through phishing emails, malicious downloads, or trojanized software installs. Once active, the infostealer silently extracts a broad range of sensitive data (as we discussed above).
This data is then exfiltrated to attacker-controlled servers where it is then sorted, again, with remarkable fidelity, often down to individual browser profiles or application-level folders. This raw information is parsed into standardized formats such as “URL:username:password” or “URL:email:password” – commonly referred to as ULP (URL:Login:Password) format.
At this point, the data is packaged and ready for market – either sold as complete stealer logs or processed into combolists for wider distribution and monetization.

In the above chart, we see the propagation of a given credential (username and password combination) over time. Usually we observe a credential pair appear first in a stealer log prior to multiple appearances across different combolists. Occasionally, we also observe credentials that appear in combolists before we observe the stealer log where they originated be distributed.
The economics of credential theft
Once parsed, stolen credentials become commodities in a layered and highly optimized underground economy. High-quality logs – those that are fresh, complete, and potentially tied to valuable services – are considered premium goods and are often stolen by traffer teams. These logs are often sold directly to initial access brokers or vetted buyers who specialize in rapid monetization, such as account takeover, fraud, or lateral movement into enterprise networks.
In contrast, lower quality or older data is often aggregated into combolists and sold in bulk. These credentials may lack novelty, have limited value, or be partially invalid, but they remain useful for large-scale credential stuffing and other low-effort attacks.
This market stratification mirrors the lumber industry: premium logs (i.e., stealer logs with valuable access) are sold as high-end timber, while the damaged or lower-grade logs are ground down into particle board – mass-produced and widely sold.
In this analogy, combolists are the particle board of the credential theft ecosystem: cheap, widely distributed, and made from material that can’t fetch a premium on its own but has value when ground up and combined.
A look inside modern credential trading
- Telegram
- Cybercrime forums
- Subscription-based services
Here’s a little preview of what combolist activity on each of these platforms looks like.
The Telegram messaging platform
Telegram is a messaging platform known for its strong privacy features like secret chats and encrypted calls. Cybercriminals often use it to coordinate activities, distribute illicit tools, and share stolen data – including data from combolists.



The two above images show the typical Telegram based combolist channel; many free files offered in hopes that subscribers will be interested in purchasing their higher-quality data.



Even more common are advertisements from threat actors featuring premium offerings of both stealer logs and combolists. Typically, if a threat actor is running their own infostealer campaign and selling the logs generated, they will also sell the stealer-derived combolists as a secondary revenue stream. In the above image, we see a threat actor providing samples of both their combolists and stealer logs as well as pricing for private, premium subscriptions.
Cybercrime forums
Online hacking and crime forums are typically regional or language-specific (for example catering to Russian- or Chinese-speaking threat actors). Some might also focus on certain topic areas like credit card theft. Typically, users need to purchase credits, paid memberships, or invite-only access to use these forums in any meaningful capacity.


Subscription-based services
Subscription services deliver curated, regularly updated combolists and stealer logs – sometimes even streaming stolen-data in near real-time. Delivery of this data is often done through Telegram but can also be seen uploaded to a personal site run by the threat actor or special access forums.

Many forums offer exclusive access to private, higher quality combolists and other breaches. Depending on the quality, monthly subscriptions trend around $20 USD with lifetime subscriptions costing up to $400 USD.
To maximize profit, threat actors often maintain multiple identities or storefronts, rebranding the same datasets under different aliases across Telegram and forums. This dynamic, segmented marketplace turns credential theft into a scalable and repeatable business model – one where every log, no matter the quality, finds a use or a buyer.
Quantifying the threat: Data-driven insights about the rise of ULPs
In our previous analysis of combolists, we compared several traditionally formatted combolists to our collection of stealer logs and saw very little overlap – typically just 1–2% of the credentials appeared in both sources.
With newer ULP combolists, that is no longer the case. Recent tests on randomly selected ULP combolists from our data lake show a dramatically higher intersection with more like 30%-60% overlap with stealer logs:

60% of credentials in the example above were also present in stealer logs, mainly from Redline and LummaC2.

46% of credentials in this example overlapped, driven largely by the Vidar infostealer.

Although this analysis is limited to three samples, the pattern is consistent when searching ULP combolists against our existing dataset. Single-digit overlap between combolists and stealer data is rare – from this, we can infer that modern combolists are being assembled directly from stealer-log data.
What criminal usage of these combolists means for defenders
Cybercriminals’ increased reliance on stealer-derived combolists represents a significant escalation in credential-based threats, bringing immediate and profound real-world consequences. Individuals face rapid compromise of personal accounts, social media profiles, and financial services, while corporations risk serious breaches due to credential reuse as well.
Addressing these threats demands sophisticated, proactive defense measures. Organizations should:
- Leverage real-time credential monitoring and automated remediation systems capable of immediately detecting and neutralizing exposed accounts
- Move beyond basic MFA and adopt phishing-resistant authentication methods such as hardware security keys (e.g., FIDO2/WebAuthn) and conditional access policies to robustly mitigate credential-stuffing effectiveness
- Remain diligent about advanced threat detection, stringent password management solutions, and continuous employee training
REQUEST A DEMO
SpyCloud shows you what criminals have in hand, before they can act
Get a leg up with the industry’s most powerful exposure insights – sourced from infostealer logs, phished data, ULP combolists, and breaches.






